Monitoring and Securing
Your Networks
The AEGIS Cybersecurity Operations Center
Stay Ahead of Emerging Threats
Real-Time Threat Detection
Every IP associated with an attack is immediately logged, traced, and analyzed, leveraging our AI-driven detection capabilities. This ensures that no breach attempt goes unnoticed, providing a proactive defense system.
Automated Threat Mitigation
Aegis Defender Pro’s unique auto-mitigation technology allows for real-time updates to your firewalls, automatically blocking known malicious IPs and preventing threats before they reach your network.
Ransomware Protection
Our system proactively identifies and blocks known ransomware servers, while our advanced ransomware protection offers additional layers of defense, ensuring your network is shielded from all types of ransomware attacks.
Endpoint Protection and Security Updates
Every endpoint in your network is safeguarded with real-time firewall updates. Our service ensures that any new threats are immediately blocked across all devices, providing seamless protection for all your assets.
Comprehensive Security Audits and Reporting
We offer detailed security assessments and real-time reporting, giving you full visibility into your network’s security status. With our services, you’ll always know where vulnerabilities lie and how to address them.
Advanced AI-Driven Threat Intelligence
Our solution leverages cutting-edge AI to detect and respond to evolving threats, reducing false positives and ensuring accurate, efficient threat mitigation. This guarantees maximum uptime and minimal interruptions to your operations.
Attack Detection
Our platform identifies malicious activity in real-time, detecting threats as soon as they emerge within any network or endpoint.
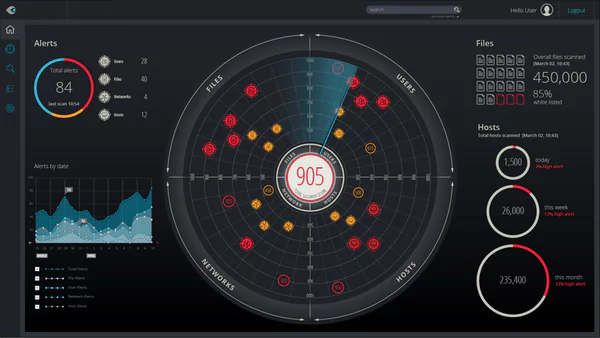
Real-Time Detection & Response
In today's rapidly evolving threat landscape, Aegis Defender Pro ensures your network is always equipped to detect and mitigate even the most sophisticated attacks. Leveraging advanced AI-driven technology, we provide real-time monitoring and threat detection across all endpoints. Our solution detects suspicious behavior and known attack patterns across your network, ensuring a proactive response to potential security incidents.
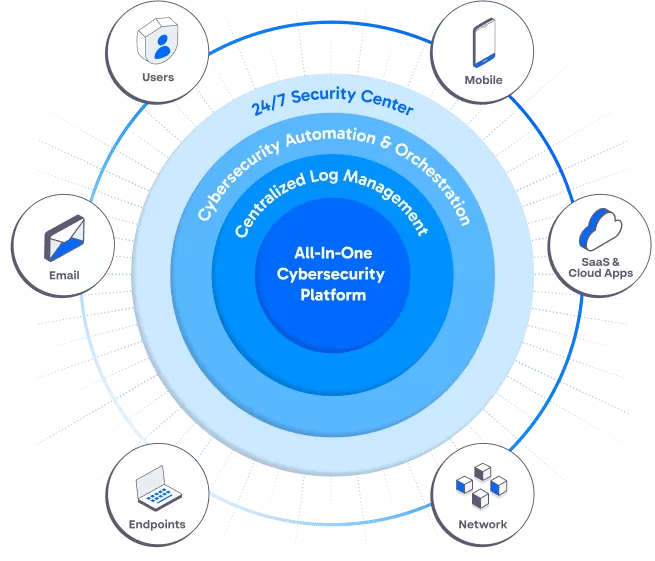
Key Features
-
24/7 Real-Time Threat Detection: Our platform continuously monitors your environment, identifying malicious activity and responding instantly to potential threats before they can cause harm.
-
Advanced AI and Machine Learning: AI-driven algorithms analyze patterns and detect anomalies across your network, providing a higher degree of accuracy and reducing false positives.
-
Behavioral Analytics: Monitoring user behavior and system activity allows us to identify abnormal patterns indicative of insider threats or external attacks, ensuring no malicious activity goes unnoticed.
-
Comprehensive Coverage Across All Endpoints: Protect every device, server, and application within your network with robust detection mechanisms that work in unison, ensuring nothing slips through the cracks.
Tracing and Research
Once a malicious IP is detected, we go beyond standard tracing
IP Detection
As soon as an attack is identified, the malicious IP is flagged for further investigation. Our team immediately isolates this IP and traces it to it's source and running it through multiple abuse databases.
Advanced CIDR Analysis
We don't just stop at the IP. Aegis Defender Pro performs advanced CIDR (Classless Inter-Domain Routing) analysis, tracing the attack back to its broader network. This helps us capture entire blocks of malicious IP addresses, providing a more robust defense.
Research and Validation
Every new IP or CIDR identified undergoes a rigorous validation process before being added to our Master Block List. Our research team, backed by AI tools, ensures only confirmed threats are blocked, reducing the chance of false positives.
The Master Blocklist
Our Master Blocklist is the culmination of years of work from thousands of sources around the world. Combining databases from abuse reporting websites, Government sources and cyber-attacks on our own clients, we've created one of the most comprehensive lists of IP addresses and CIDRs used by C2 Commanders, Bot-Nets, Spammers, Hackers and Malware / Ransomware servers.
When installed, Aegis Defender Pro downloads and applies the MBL to the Windows Defender Firewall, instantly protecting the endpoint from over 800 million malicious actors worldwide.

Firewall Updates
Aegis Defender Pro automates firewall updates across all endpoints, ensuring every network is shielded with the latest attack data, within minutes of an attack.
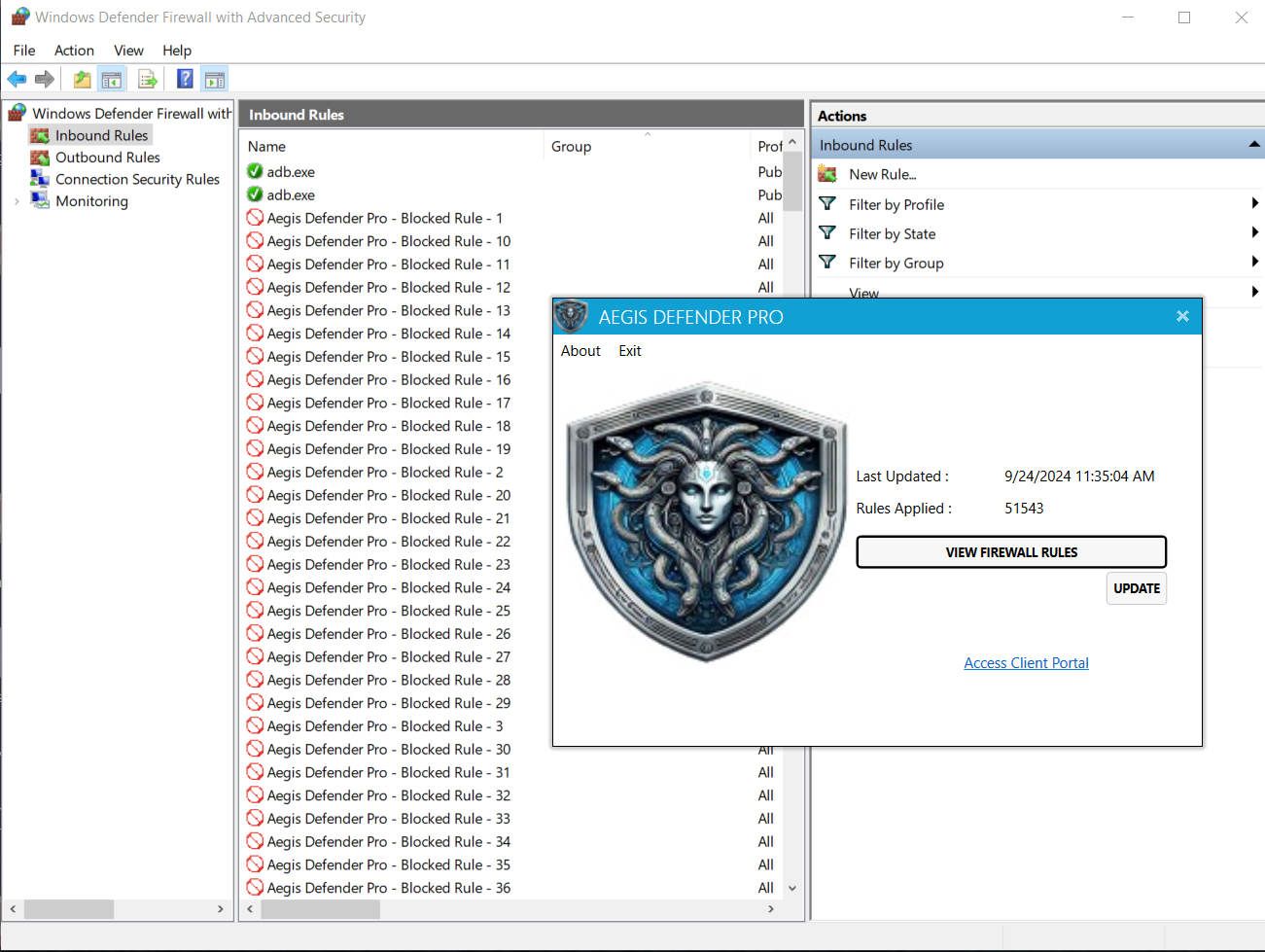
Comprehensive Network Coverage: By blocking not just individual IPs but entire CIDR ranges, Aegis Defender Pro shields the entire network from potential future attacks originating from the same source.
Automated Firewall Updates: All network endpoints are automatically updated with the latest attack data, eliminating the need for manual intervention and ensuring up-to-the-minute protection.
24/7 Auto-Mitigation: The system operates around the clock, autonomously safeguarding the network from evolving threats, providing constant protection without relying on human oversight.
Treated as a Single Community
At Aegis, every subscriber becomes part of a collective defense ecosystem. Each organization not only benefits from the real-time detection and mitigation of threats but also contributes to the greater good.
Whenever an attack is identified on one network, the attack data is immediately shared across all subscribers through our crowdsourced Master Blocklist. This ensures that if one client faces a threat, all clients are instantly protected from the same source.
It’s a community-based defense approach where the more attacks we face together, the stronger and more resilient every network becomes. Our solution unites businesses, governments, and institutions into a singular, collaborative cybersecurity shield, where each member plays an essential role in enhancing protection for all.
Crowdsourced Attack Data
The Aegis team continuously monitors attacks across our entire subscriber base using advanced SIEM systems, server logs, and a comprehensive array of security solutions.
Synchronized
Firewalls
Aegis Defender Pro automates firewall updates across all endpoints, ensuring that every network connected to Aegis benefits from the latest threat intelligence.
Unmatched Collaboration
When one subscriber is attacked, Aegis ensures that every other subscriber is automatically protected within minutes—providing a layer of proactive defense no other cybersecurity solution can offer.
Comprehensive Compliance and Security Standards
At Aegis Cyber Defense Systems, compliance isn’t just an added feature—it’s a cornerstone of our cybersecurity strategy. Aegis Defender Pro is designed with the highest governmental and industry compliance standards in mind, ensuring that your organization meets and exceeds requirements while maintaining superior protection.
Government and DoD Compliance
Our platform is fully aligned with the stringent requirements set by the Department of Defense (DoD) and the broader U.S. government. As we expand our services through Managed Security Service Provider (MSSP) offerings, we ensure that our technologies adhere to NIST SP 800-53, NIST SP 800-171, and CMMC (Cybersecurity Maturity Model Certification), among other key frameworks. This guarantees that sensitive data remains secure and protected across all environments, especially when managing critical infrastructure for military or governmental entities.

Cybersecurity Frameworks
In addition to DoD-specific standards, Aegis Defender Pro operates under the best practices outlined in frameworks like ISO 27001, HIPAA, GDPR, and PCI-DSS. This makes Aegis the perfect solution for government, military, healthcare, and financial institutions, offering an all-in-one solution that mitigates risk and simplifies compliance reporting.

Automated Compliance Updates
Our auto-mitigation tool does more than protect your network—it also helps maintain compliance by automatically applying updates to firewalls and systems in line with new regulatory requirements. This reduces the administrative burden of manual updates and ensures your organization is always in alignment with the latest standards.

Proactive Defense Against Compliance Breaches
With real-time, 24/7 monitoring and automated mitigation of threats, Aegis reduces the risk of non-compliance by preventing unauthorized access to sensitive systems and ensuring critical information remains protected. Our platform helps maintain the integrity of audit trails and log management, providing an essential layer of defense that strengthens your overall compliance posture.
Solutions for All Sized Organizations
From our stand-alone product, Aegis Defender Pro, to our Enterprise Platform, all benefit from attack data from any client.
Aegis Defender Elite
Aegis Defender Enterprise
What Our Customers Say

19 Years of Unbreached Security and Optimal Performance
As a client of Charlie and now Aegis for over 19 years, I can confidently say that their service and protection has been nothing short of exceptional. My servers came under attack back in 2018, and Charlie fought off the attackers, one by one. The Master Block List, now part of Aegis Defender Pro, has been a game changer. I haven’t experienced a single breach, and my performance is consistently excellent.
Aegis has transformed from those early days into the sophisticated solution it is today, and my company has benefited from being a part of that journey. I can't recommend Aegis Cyber Defense Systems enough for anyone looking to secure their servers with real-time protection.

Rescuing and Securing a Non-Profit: How Aegis Brought Us Back from a Devastating Hack
Back in 2017, we faced a catastrophic breach when our WordPress site, hosted on our network and accessed by remote employees, was hacked. As a non-profit organization, we didn’t have the resources to bring in a large team for repairs. That’s when Charlie Trig (then known as Hacker Blocker) stepped in.
Charlie found the hack, fixed it, restored backups we didn’t even know we had, and performed a full repair on our Intranet system. Since using Aegis, we’ve had zero attacks. The protection and peace of mind they’ve provided are invaluable, and our performance has been consistently flawless. Thanks to Aegis, we’ve been secure like never before.

Unparalleled Expertise, Trust, and Lifelong Partnership
I cannot thank Charlie and Aegis Cyber Defense Systems enough for their unmatched expertise, unwavering commitment to customer service, and deep understanding of my unique needs. It truly feels like divine intervention led me to Aegis, and I am forever grateful.
Charlie has been my hero for over 8 years, riding in on his white horse just when I needed him the most. Not only did Aegis protect my business with their cutting-edge solutions, but Charlie also uncovered a critical flaw in my site’s code that even the original developers missed. The level of dedication and detail he brings is rare, and his work has spared not just me but countless others from frustrations we didn’t even know we had.



