Enterprise Cybersecurity Solutions
Our Enterprise & Elite Packages deliver next-level defense with the power of real-time auto-mitigation, for complete protection across your networks.

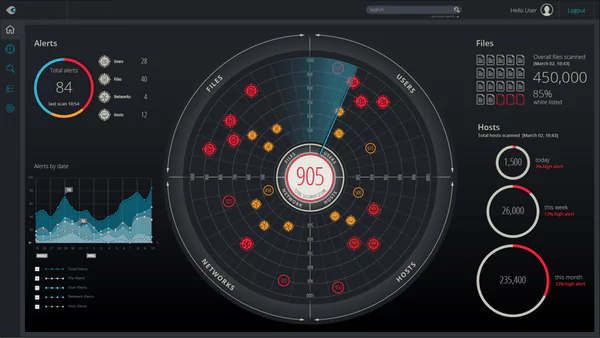
Detect and Block Cyber Threats Instantly
Aegis Defender Platform blocks up to 99% of malicious traffic instantly, detects and reports new attacks, and updates Endpoint firewalls within minutes.

Affordable Cybersecurity for Small Business
Aegis Defender Pro costs only $10 per month per seat, allowing SMBs to protect themselves with attack data from larger organizations.

Advanced Ransomware Protection
Aegis Defender Pro offers robust real-time firewall updates, ensuring protection against known ransomware servers before they can breach your system.

AEGIS DEFENDER
All-in-One Cybersecurity Platform
Automatic Cyber Defense at Every Endpoint
At Aegis Cyber Defense Systems, we deliver more than just comprehensive cybersecurity solutions. Our flagship platform, Aegis Defender Pro, sets us apart with its Auto-Mitigation technology, a groundbreaking system that synchronizes firewalls across all client networks, automatically neutralizing threats within minutes of detection on just a single endpoint.
The Aegis Advantage
Aegis Defender Pro blocks up to 99% of malicious traffic across your network by leveraging a comprehensive Master Blocklist containing over 800 million IPs reported for malicious activity. Our cutting-edge Managed Security Services ensure that attacks are detected, mitigated, and shared across all subscribers in real-time, allowing for immediate updates to every endpoint in your network. With Aegis, cyber threats are not only blocked—they are automatically neutralized to protect your business, 24/7.
Aegis Defender Pro
Aegis Defender Pro is our proprietary software to update Windows Defender's built-in firewall. It automatically updates the firewall's rules every 30 minutes using our Master Block List, ensuring your network is protected from malicious IP addresses in real-time.
Aegis Defender Elite
Aegis Elite offers enhanced cybersecurity with 24/7 Managed Detection and Response (MDR) services. Designed for businesses needing advanced threat detection, this solution includes AI-driven analytics, proactive monitoring, and real-time remediation to stop attacks before they impact your operations.
Aegis Defender Enterprise
Aegis Enterprise provides full-spectrum security for large-scale organizations. In addition to MDR, Enterprise includes customizable security policies, forensic analysis, and advanced endpoint protection. It’s built for enterprises seeking comprehensive, scalable defense across their entire network.
What Our Customers Say

19 Years of Unbreached Security and Optimal Performance
As a client of Charlie and now Aegis for over 19 years, I can confidently say that their service and protection has been nothing short of exceptional. My servers came under attack back in 2018, and Charlie fought off the attackers, one by one. The Master Block List, now part of Aegis Defender Pro, has been a game changer. I haven’t experienced a single breach, and my performance is consistently excellent.
Aegis has transformed from those early days into the sophisticated solution it is today, and my company has benefited from being a part of that journey. I can't recommend Aegis Cyber Defense Systems enough for anyone looking to secure their servers with real-time protection.

Rescuing and Securing a Non-Profit: How Aegis Brought Us Back from a Devastating Hack
Back in 2017, we faced a catastrophic breach when our WordPress site, hosted on our network and accessed by remote employees, was hacked. As a non-profit organization, we didn’t have the resources to bring in a large team for repairs. That’s when Charlie Trig (then known as Hacker Blocker) stepped in.
Charlie found the hack, fixed it, restored backups we didn’t even know we had, and performed a full repair on our Intranet system. Since using Aegis, we’ve had zero attacks. The protection and peace of mind they’ve provided are invaluable, and our performance has been consistently flawless. Thanks to Aegis, we’ve been secure like never before.

Unparalleled Expertise, Trust, and Lifelong Partnership
I cannot thank Charlie and Aegis Cyber Defense Systems enough for their unmatched expertise, unwavering commitment to customer service, and deep understanding of my unique needs. It truly feels like divine intervention led me to Aegis, and I am forever grateful.
Charlie has been my hero for over 8 years, riding in on his white horse just when I needed him the most. Not only did Aegis protect my business with their cutting-edge solutions, but Charlie also uncovered a critical flaw in my site’s code that even the original developers missed. The level of dedication and detail he brings is rare, and his work has spared not just me but countless others from frustrations we didn’t even know we had.
Minimum Effort, Maximum Protection
Why complicate your cybersecurity stack with multiple, expensive tools? With Aegis Defender, you get a streamlined, fully automated platform that delivers all the essential protection your network needs in one solution. Backed by our team of experts 24/7, Aegis ensures real-time threat detection and auto-mitigation, keeping your systems secure without the complexity.

Real-Time Detection & Breach Protection
- Breach Protection: We don’t just detect; we mitigate in real-time, making sure threats are blocked across every firewall in your network, using Aegis' centralized management for total visibility.
- Reduced Downtime: Our combined approach reduces the time and effort needed to respond to threats, ensuring that your IT team remains focused on core operations.
- Tailored Solutions: Whether you're in the commercial, municipal, or government sector, our MSSP service ensures scalable, customizable protection designed specifically for your needs.
Elite and Enterprise Packages
Through our strategic partnerships, we now offer full Managed Security Service Provider (MSSP) services. This means more than just monitoring and detection. Aegis Cyber Defense Systems now offers a complete suite of services that protect your infrastructure from breaches before they occur. With AI-driven threat detection and comprehensive security analytics, Aegis acts as the missing piece in the cybersecurity puzzle, offering the unique capability of auto-mitigation of threats across all networks.
Compliance and Security Standards
At Aegis Cyber Defense Systems, compliance isn’t just an added feature—it’s a cornerstone of our cybersecurity strategy. Aegis Defender Pro is designed with the highest governmental and industry compliance standards in mind, ensuring that your organization meets and exceeds requirements while maintaining superior protection.
With real-time, 24/7 monitoring and automated mitigation of threats, Aegis reduces the risk of non-compliance by preventing unauthorized access to sensitive systems and ensuring critical information remains protected.

Ransomware Defense
Aegis Defender Pro offers robust real-time firewall updates, ensuring protection against known ransomware servers before they can breach your system. As part of our comprehensive security services, our platform integrates advanced ransomware protection, leveraging state-of-the-art detection capabilities to stop ransomware attacks in their tracks.
The Aegis Platform provides advanced ransomware protection by enhancing visibility across endpoints, networks, and users. This ensures that ransomware is detected in the earliest stages of an attack, allowing Aegis to immediately respond and neutralize the threat. With the capability to auto-mitigate across critical system components, Aegis Defender Pro prevents ransomware from encrypting files or drives, stopping the attack cycle before it can cause harm. This proactive approach delivers unparalleled protection, safeguarding your network from even the most sophisticated ransomware threats.
Centralized Log Management (CLM)
Aggregate and analyze log data from across your network to support threat hunting, compliance, and forensic investigations, providing deep visibility into security events.
Extended Detection and Response (XDR)
Correlate data from multiple sources, including endpoints, networks, and cloud environments, to enhance detection of sophisticated attacks and improve response efficiency.
Security Orchestration, Automation, and Response (SOAR)
Automate and streamline security workflows, coordinating responses across your entire environment to ensure swift and efficient threat mitigation.
Managed Detection and Response (MDR)
Outsource your Security Operations Center (SOC) to a dedicated team of experts who provide round-the-clock monitoring, detection, and response to cyber threats.
Email Security
Protect your organization from phishing, malware, and other email-borne threats by monitoring incoming emails for malicious content and blocking risky senders.
Port Scanning
Identify and secure open and vulnerable ports across your network, preventing malicious actors from exploiting these entry points to launch attacks.
SaaS Security Posture Management (SSPM)
Continuously monitor and manage the security posture of your SaaS applications, ensuring compliance and reducing risks across cloud-based environments.
Cloud Security Posture Management (CSPM)
Identify and remediate security risks within cloud applications and services, ensuring that your cloud infrastructure remains secure and compliant.
Mobile Threat Defense (MTD)
Protect mobile devices from cyber threats by detecting and blocking malicious apps and rogue activities in real-time, ensuring secure mobile operations across your network.
Network Detection & Response (NDR)
Identify and neutralize hidden threats moving through your network, leveraging advanced detection tools to uncover lateral movements and stop attacks before they spread.
User Behavior Analytics (UBA)
Monitor user activity to detect abnormal behaviors that may indicate insider threats or malicious actors, preventing security breaches through behavioral intelligence.
Deception
Set up decoy systems such as fake files, endpoints, and networks to lure attackers, exposing their tactics and providing early warnings of potential threats.
Domain Filtering
Block access to malicious websites and domains, safeguarding users from phishing attacks and malware downloads by preventing dangerous web interactions.
Endpoint Protection (EPP)
Combine Next-gen Antivirus (NGAV) and device control measures to protect endpoints from a range of threats, including malware, ransomware, and unauthorized access.
Endpoint Detection & Response (EDR)
Monitor endpoints continuously to detect advanced threats and take immediate action to remediate malware and other security risks across all connected devices.